High Performance Block Magnets for Motor
Material: The cheapest magnetic material, main contents including ferric oxide, barium and strontium.
Grade:highest to FB9B, FB9N, FB14H
Magnet Shape: Block shape and more Customized shapes are available with hundreds of existing mould.
Features: A competitive cost alternative to other magnetic materials, offers relatively high operating temperatures and good resistance to corrosion & demagnetization. However, it has lower energy levels (Br) and is brittle in nature.
Applications: Auto Industry: EPS power steering motor, fan motor, starter motor, wiper motor, window motor, seat motor
Househould Appliances: Soymilk Machine, Juicer Machine, Egg Mixer, Kitchenware Motor, Air-Conditioner.
Fitness Equipment: Treadmills, Massage Chairs
Block Ferrite Magnet,Neodymium Block Magnets,Customize Ferrite Block Magnet,Block Ring Ferrite Magnet Chongqing Great Well Magnet Co.,ltd. , https://www.gwmagnet.com
While the Internet of Things brings convenience to people's lives, it also brings many security problems to people.
According to statistics, the number of globally connected devices in 2010 was 2 billion, which is expected to increase to 25 billion in 2020. Network experts believe that with the increasing number of connected devices and the increasing popularity of technology, the "black" of the Internet of Things is an "inevitable" problem.
It is understood that the active defense platform of the company has been the first in China and has filled the gap in the IoT attack defense technology, while meeting the security needs of Internet of Things in various industries, such as: government, safe city, smart city. , finance, military, military, energy, manufacturing, transportation, enterprises, petroleum and petrochemicals, etc.
   Proactively discovering IoT device vulnerabilities

   value of customer

With the rapid development of the Internet of Things, the Internet of Things has been able to connect physical devices, vehicles, buildings and some other embedded electronic devices, software, sensors and other things to the network, enabling these objects to collect and exchange data. The Internet of Things allows remote systems to sense and control things through existing network infrastructure, and integrate the physical world into computer systems to increase efficiency, accuracy, and economic benefits. The Internet of Things has gradually integrated into our lives.
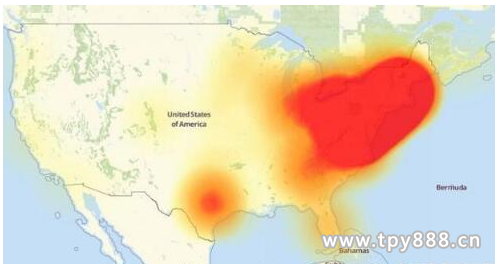
On October 21, 2016, the US East Coast region suffered from a large network, due to the strong DDoS attack on the day of the US domain name resolution service provider Dyn. Dyn said that the DDoS attack involves tens of millions of IP addresses. The most important attack comes from IoT devices. According to ISP service provider Level3, there are 500,000 IoT devices infected by Mirai worldwide. The attack was a complex attack that spanned multiple attack vectors and Internet locations. One of the sources of attack traffic was analyzed to be infected with Mirai zombies because the IP address of some discrete attacks came from the Mirai botnet. After this incident, it has aroused great attention to the security of the Internet of Things in the world. The scope of attacks on the Internet of Things has moved from the first individual to a large-scale attack, and the attack situation has become more and more complicated.
So how can we prevent it from happening, how to make the Internet of Things security problem smash in the cradle at the moment of the Internet of Everything?
Based on the current IoT security pain points, the company has conducted in-depth research on IoT security incidents in recent years, and independently developed the IoT threat detection and active defense platform (hereinafter referred to as the active defense platform), which can efficiently and timely discover IoT devices. There are security risks and early warnings, while providing a variety of active defense measures to protect the Internet of Things security.
The current number of IoT devices is growing at an extremely fast rate. Both device manufacturers and device users have weak security awareness. Device vulnerabilities are not discovered and updated in time. Most device users pay more attention to functions. Rather than the security of the device, the attacker exploits this point and takes the appropriate attack by exploiting the known or unknown vulnerability of the device to gain control.
By actively detecting the vulnerability of the IoT device, the device weakness can be discovered in advance, and after the corresponding remedial measures are taken, the vulnerability can be effectively prevented from being exploited by the hacker. In addition to the open IoT device vulnerabilities, the company also has its own undeveloped IoT device vulnerability library to maximize the discovery of device vulnerability information.
Real-time perception of abnormal behavior
Since the DDOS incident in North America, there have been many variants of the Mirai virus, and similar virus Trojans have emerged in an endless stream. By deploying IoT security probes, the Internet of Things virus Trojans in the network are effectively identified, and password brute force cracking is detected in real time. And timely prevent or report to the active defense platform in an early warning manner, and take corresponding defense measures.
Intrusion trapping forensics
In past security incidents, some attacks have become enough crimes, and how to collect these crimes has become a big problem. By deploying intrusion trapping devices, simulating IoT devices and customer business systems, in addition to hiding real devices, it can also trap attackers to invade the device, record all intruder attacks, and extract attack data for forensics. Collect evidence to sue intruders.
Active defense
Just by detecting threats, intrusion traps, etc., it is far from satisfying the security protection of IoT devices. Perceived threats cannot prevent threats from occurring. Active defense platforms can actively upgrade devices while discovering IoT device vulnerabilities. Patching and improving device security; once the threat behavior is discovered, the active defense platform can quickly prevent the ongoing behavior; if the device is found to be infected and has the ability to transmit to other devices, the device can be reversed and blocked. The device is further infected with other devices.
By deploying the IoT threat detection and active defense platform, you can discover the assets, vulnerabilities and threat information of IoT devices in real time, and combine active defense to kill infected devices in time to prevent infections from expanding.
The active defense platform is also suitable for large-screen display, combined with maps and positioning technology to visualize threats. Dynamic display of threat events and intrusion traps on IoT devices on the big screen provides real-time security alerts for regulators, while giving quantitative scores and safety ratings to the overall security posture of the current Internet of Things.